Single Sign On (SSO)
Learn how to connect an SSO User Account to a new or existing ClientTrack Account, or learn how configure SSO for a ClientTrack environment as an admin-level user
Table of Contents
Introduction
ClientTrack enables external Single Sign-on (SSO) providers (i.e. Azure Active Directory) to be configured so that organizations using an SSO provider can provide a convenient way for users to sign in to ClientTrack without the need to maintain a ClientTrack Username and Password. Organizations may also find it beneficial to manage users with an SSO provider when multiple independent software systems (with SSO capabilities) are being accessed by staff/volunteers within the organization.
This article will cover how a standard user can link their existing ClientTrack user to their existing SSO account or create a new ClientTrack user with an existing SSO account. It will also cover how users with the “Authentication” User Tool Access Permission can configure and manage SSO settings for the ClientTrack environment and on behalf of other users.
Overview
Single sign-on is an authentication scheme that allows a user to log in with a single ID and password to any of several related, yet independent, software systems. SSO requires configuration and trust between ClientTrack and the SSO identity provider.
Once this configuration is complete for a ClientTrack environment, upon sign in, users will be able to click a button to be redirected to the identity provider for authentication. After they authenticate, they’ll be redirected back to ClientTrack which will validate the request and allow access.
ClientTrack uses the OAuth 2.0 auth code grant flow with OpenID Connect to retrieve basic user details, such as name and email from the SSO provider.
ClientTrack Users with admin-level permissions can manage system properties related to SSO such as the ability to require all new ClientTrack Users created via SSO to go through an approval process before being able to sign in. Users with permission can toggle a User's settings between SSO-only or 'Linked users' to effect whether that user can sign in with a ClientTrack username and password once they've linked an SSO account.
Linking your existing ClientTrack User to an existing SSO account
If you already have a ClientTrack username and password, you can choose to link your ClientTrack account to your SSO account for easier sign on with your SSO credentials. If you do not already have a ClientTrack User account, you may skip this section and create a new ClientTrack User account via SSO by following steps in the below section.
To link your existing ClientTrack User to an existing SSO Account, sign in with your existing ClientTrack User credentials and follow the below steps:
- Click your user in the top-right of the application to open the user settings dialog
- Click Security Settings to open the Security Settings dialog (you may need to scroll down to see it)
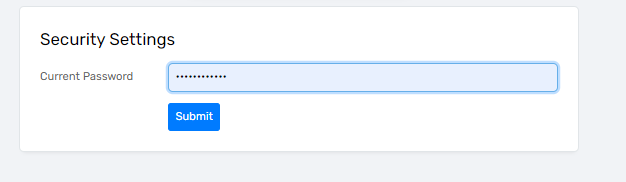
- Enter your ClientTrack password to verify that you are the account holder
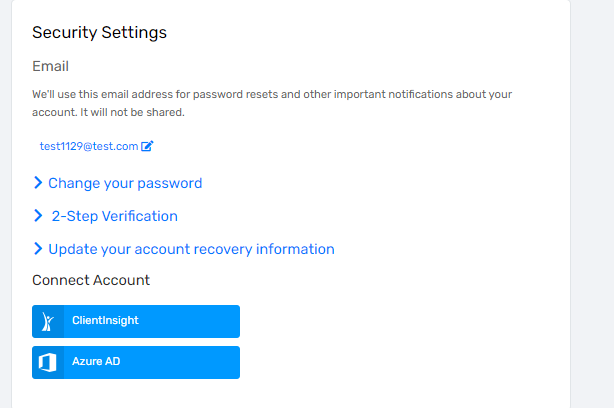
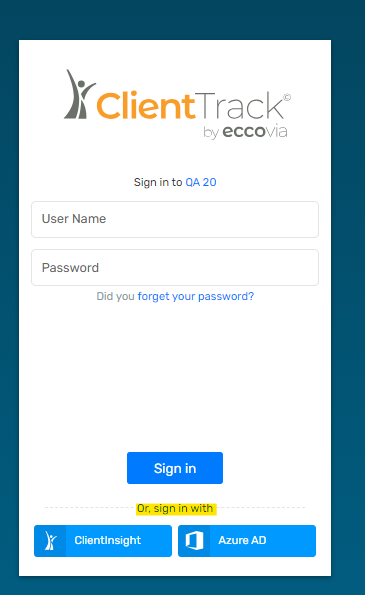
In the “Connect Account” section, click the button for your identity provider (you’ll be redirected to your identity provider to sign in). In the below example, the user's ClientTrack environment has two external SSO Accounts that they can connect to their ClientTrack User Account (ClientInsight and Azure AD).
-
- note that the Security Settings for 2-Step Verification or to Connect Account may not be visible if 2SV or SSO are not enabled for the environment
Creating a new ClientTrack User by signing in with an existing SSO account
If you have never signed in to ClientTrack before, and you sign in with SSO on the ClientTrack sign-in page, a new user account is created in the ClientTrack database and associated with the SSO account. Depending on your environment's authentication settings, this new account may require approval before you can sign in.
Important Note
If you already have a ClientTrack User and have not yet linked your SSO account to your existing ClientTrack User, DO NOT try sign in with an SSO Provider from the sign in page because ClientTrack will assume that you are creating a new user account.
If you want to link an SSO account to an existing ClientTrack account to maintain existing settings/permissions/assignments/tasks/etc., you must first sign in to the existing ClientTrack account and connect that user to the SSO account via your User's security settings. See section above for steps.
Signing on with SSO Only vs having the option to sign on with either ClientTrack or SSO
If you did not create a ClientTrack user account before signing on with SSO, you will NOT be able to sign on with a standard ClientTrack username and password - you MUST use the identity provider for sign on.
If you want to have the option to sign on with either SSO OR a standard ClientTrack username and password you must first create a ClientTrack user account, then follow the instructions below to link your ClientTrack user account to your SSO account.
Note that signing in as a standard ClientTrack user (NOT via SSO) might also require a verification code if 2-step verification is enabled or required.
ClientTrack Authentication Configuration for Admin Users
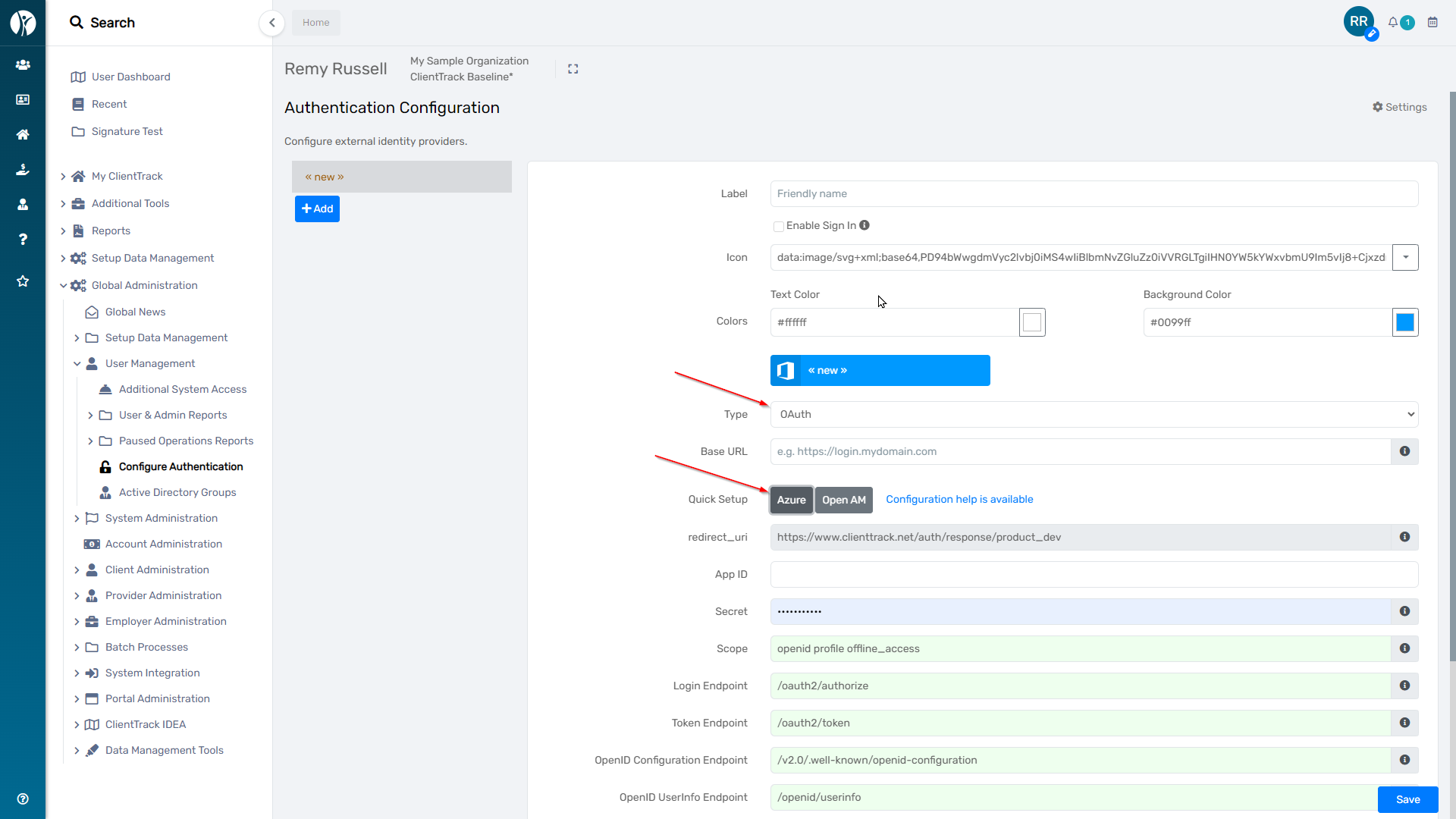
ClientTrack supports any OAuth identity provider that supports OpenID Connect. This includes Azure Active Directory (AD) and Open Access Management (OpenAM).
To configure external identity provider, navigate to the following page within the ClientTrack. Only users with the “Authentication” User Tool Access Permission will be able to access this page.
Home Workspace → Global Administration → User Management → Configure Authentication.
The OAuth endpoints can be automatically configured when you choose a Quick Setup option for Azure or Open AM, otherwise you can input the configuration details as required for another identity provider.
System Properties for Authentication
ClientTrack allows users to authenticate with an SSO identity provider or standard ClientTrack credentials depending on the System Properties and a User's settings. There are a variety of System Properties related to Authentication that can affect the user sign in process.
To configure additional Authentication settings for the System, navigate to the following page within the ClientTrack and view the Properties within the “Authentication” and “Authentication Approval” groups. Only users with appropriate permissions will be able to access this page.
Home Workspace → Global Administration → System Administration → System Properties.
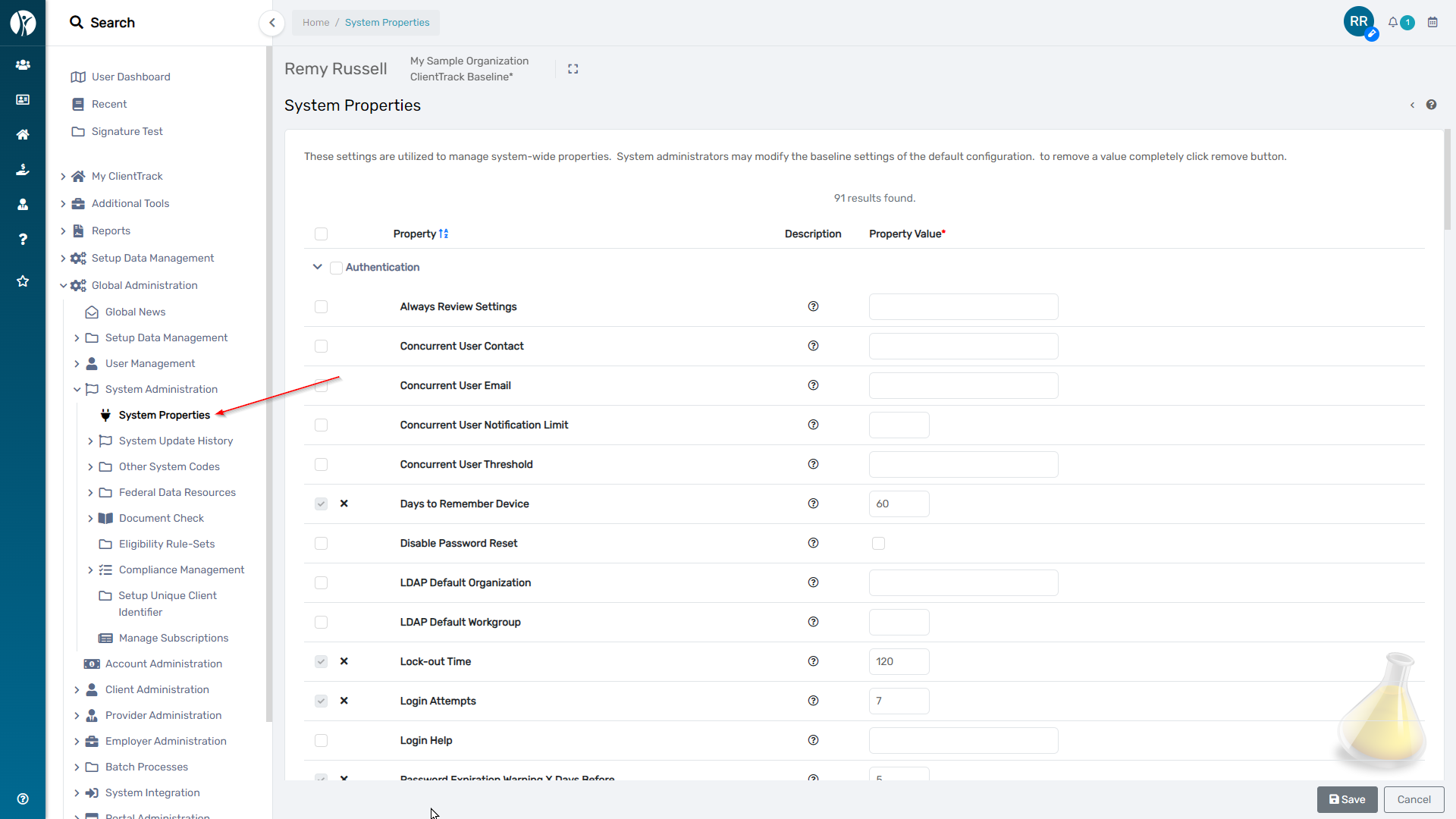
Hover over the help icon for each Property to understand its purpose,
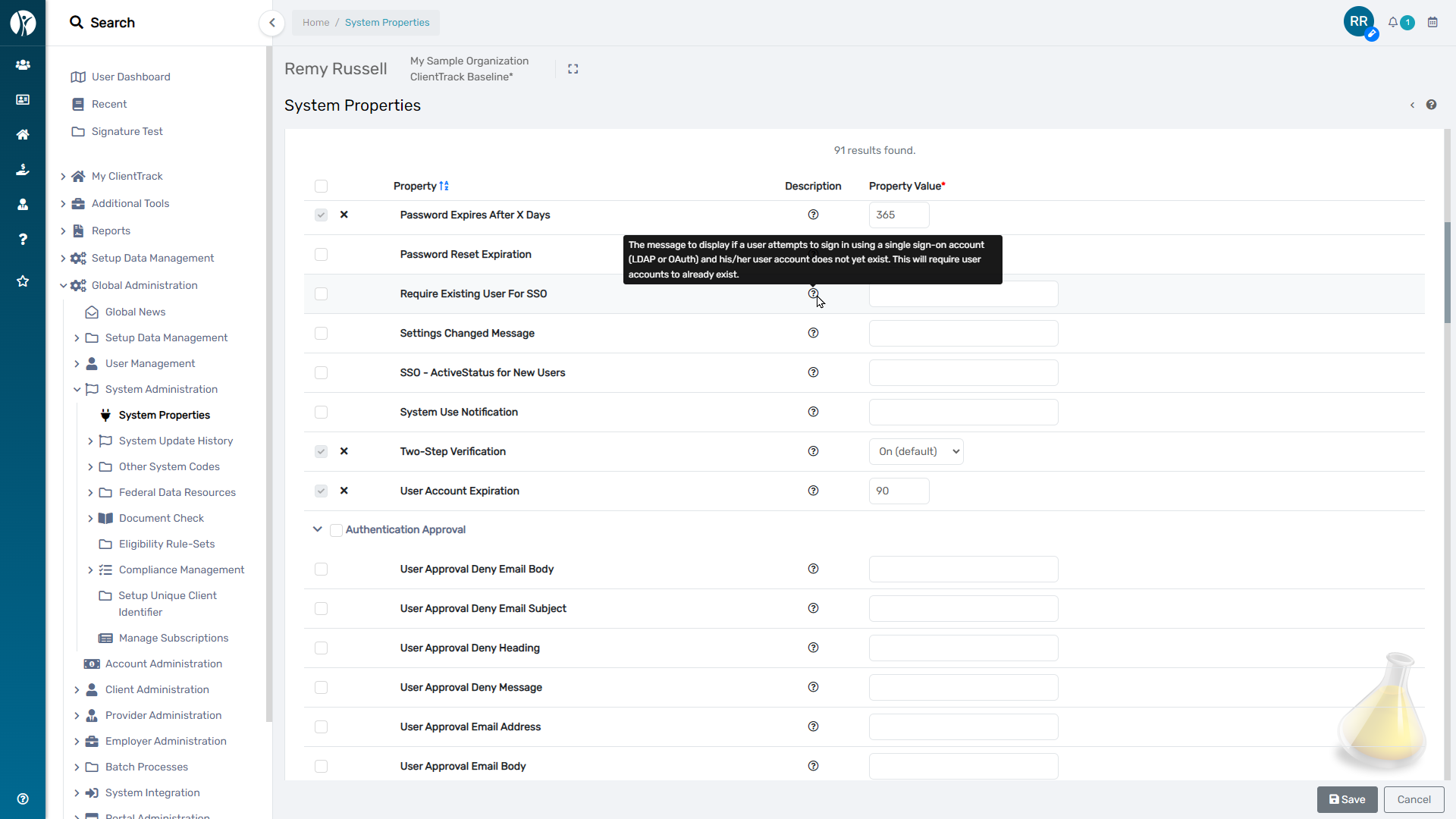
See the User Approval Process for more details about user approvals.
ClientTrack SSO Only vs Linked User Authentication Management tool for Admin Users
ClientTrack can force a user to log in via SSO (SSO-Only) or allow a user to choose between utilizing ClientTrack Sign In credentials or SSO to sign in (a “Linked User"). A ClientTrack User with permission is able to manage multiple users' Authentication Type if they want to switch users from an "SSO-only" User to a “Linked User” or the inverse.
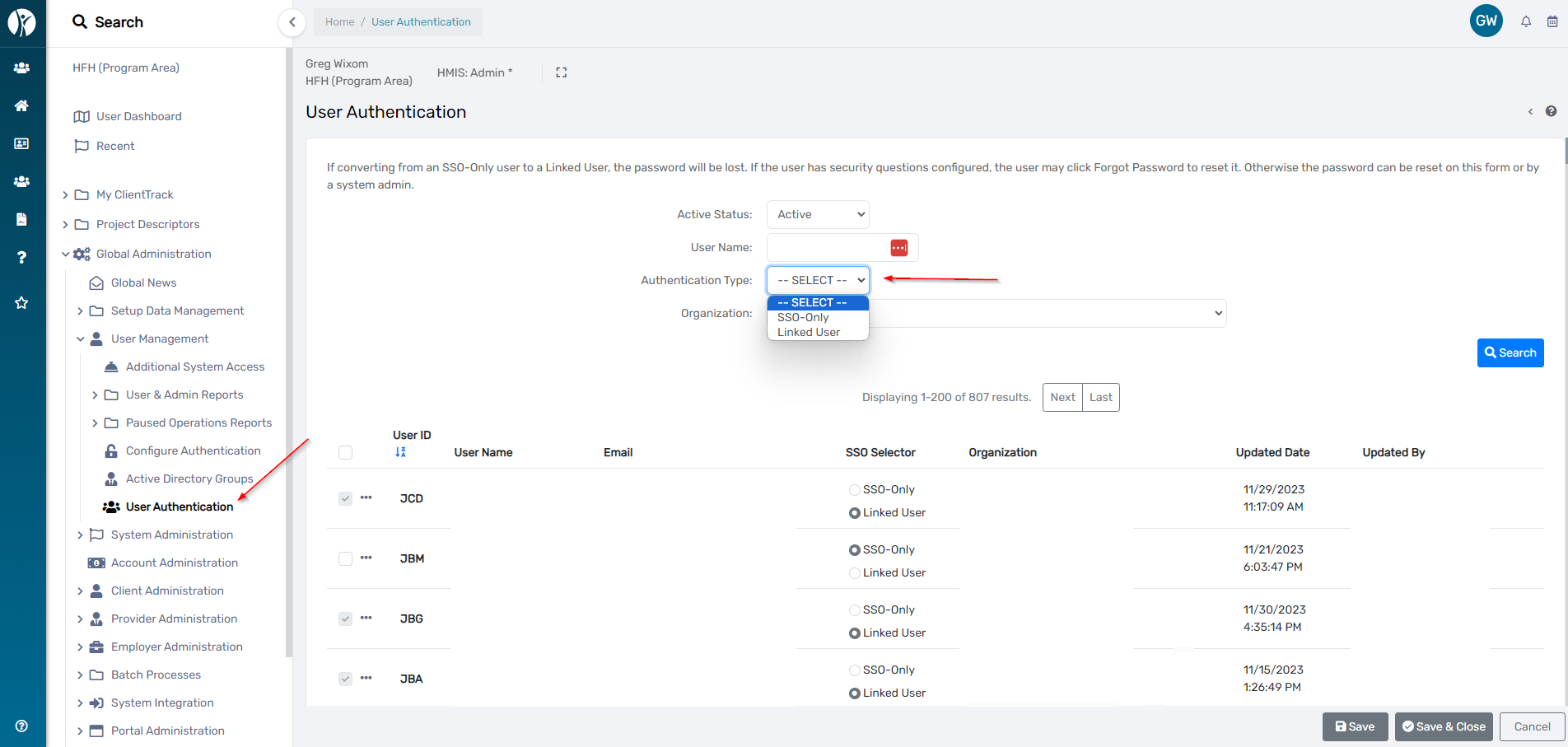
Related articles:
https://en.wikipedia.org/wiki/Single_sign-on
